How to Configure Remote Connections for PostgreSQL | Guide
To configure PostgreSQL for remote connections, you need to adjust the PostgreSQL configuration files and your system’s firewall settings. Here’s a step-by-step guide:

To configure PostgreSQL for remote connections, you need to adjust the PostgreSQL configuration files and your system’s firewall settings. Here’s a step-by-step guide:

If you’re encountering the error pnpm: command not found in your GitHub Actions workflow, it’s likely due to the environment not properly recognizing the pnpm binary. A quick and efficient way to resolve this issue is to create a symbolic link (ln) for pnpm from its installed path to /usr/local/bin/.

In this tutorial, we will create a React component that detects if a user is accessing the app from a mobile device.
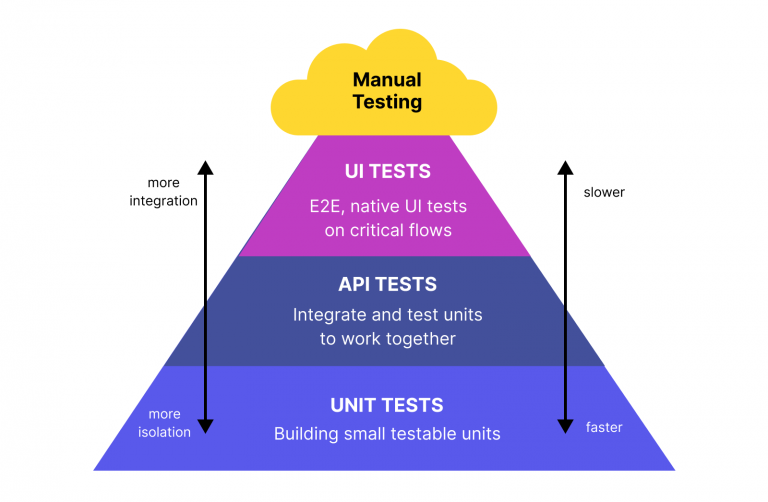
Learn how to set up alias imports like @ in Jest with TypeScript for cleaner, organized code. Follow this tutorial for easy configuration.

Learn how to set up and execute end-to-end (E2E) API testing using Jest, Axios, and TypeScript. This step-by-step guide covers everything from installation and configuration to writing and running your tests, ensuring your API functions correctly in all scenarios. Perfect for developers looking to improve their API’s reliability with robust testing practices.
Designing machine-to-machine (M2M) authentication strategies in a Node.js, TypeScript, and Express application involves securely authenticating one service to another without user interaction. Here’s an outline of common strategies:

Tìm hiểu sự khác biệt chính giữa Kubernetes (k8s), k3s và Minikube. Khám phá công cụ quản lý container nào phù hợp nhất với môi trường phát triển, sản xuất hoặc tài nguyên hạn chế của bạn.

SSH (Secure Shell) keys are crucial for secure access to servers and other systems. Generating SSH keys on a Linux system is a straightforward process. This tutorial will guide you through the steps to generate, configure, and use SSH keys for secure access.

To increase the sudo timeout in Linux, you need to adjust the timestamp_timeout setting. This setting controls the amount of time, in minutes, that a user’s sudo authentication remains valid before requiring re-authentication.

Setting up the ELK Stack (Elasticsearch, Logstash, and Kibana) on Ubuntu involves several steps. Here’s a guide to help you through the process: